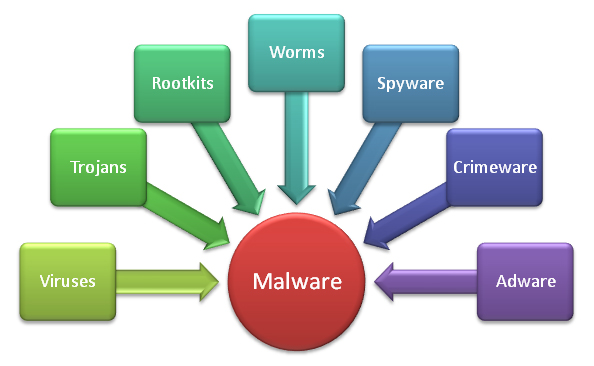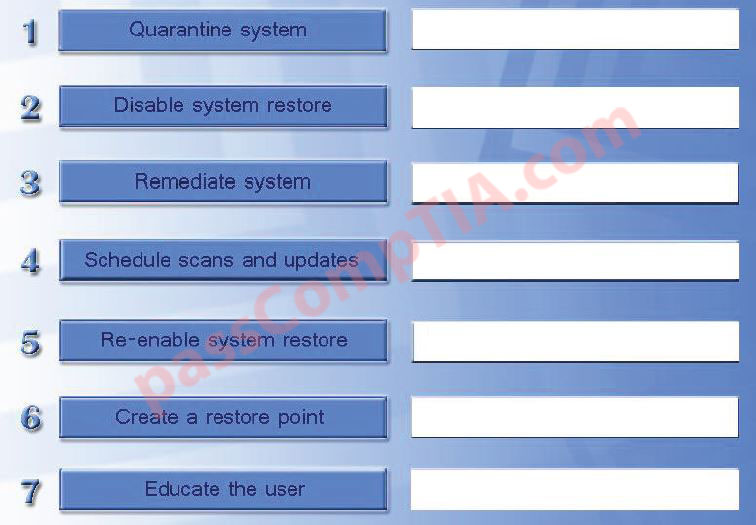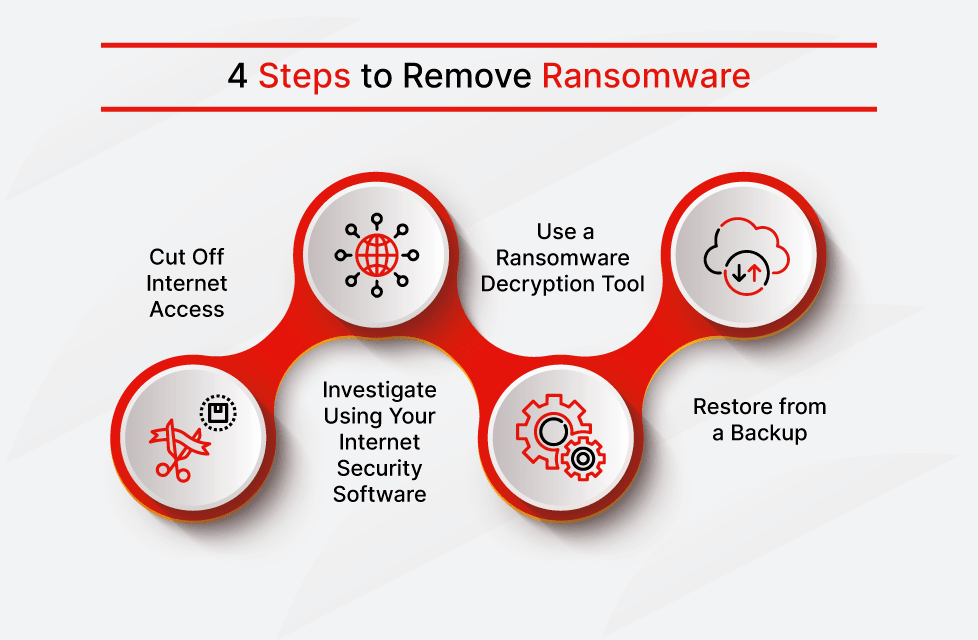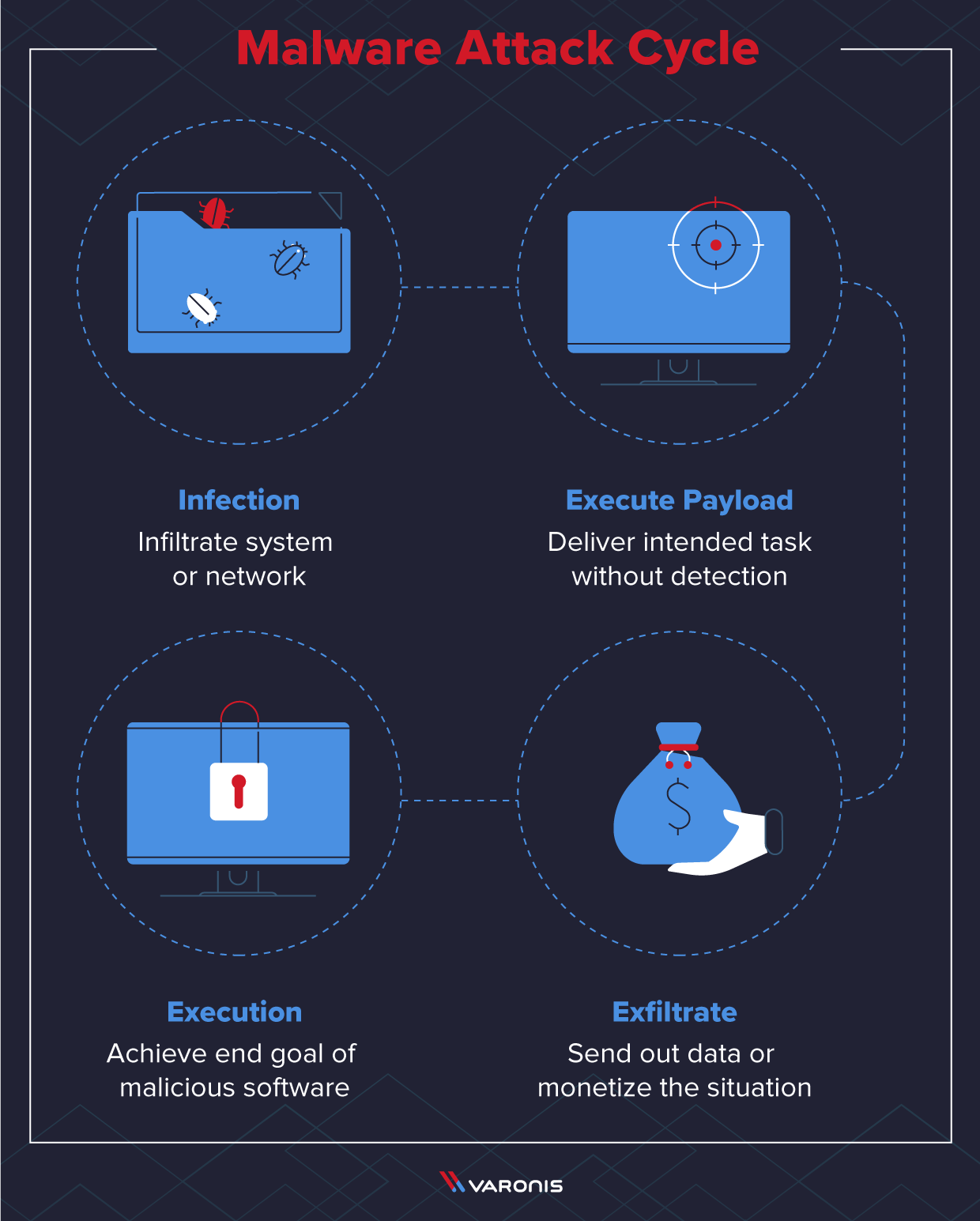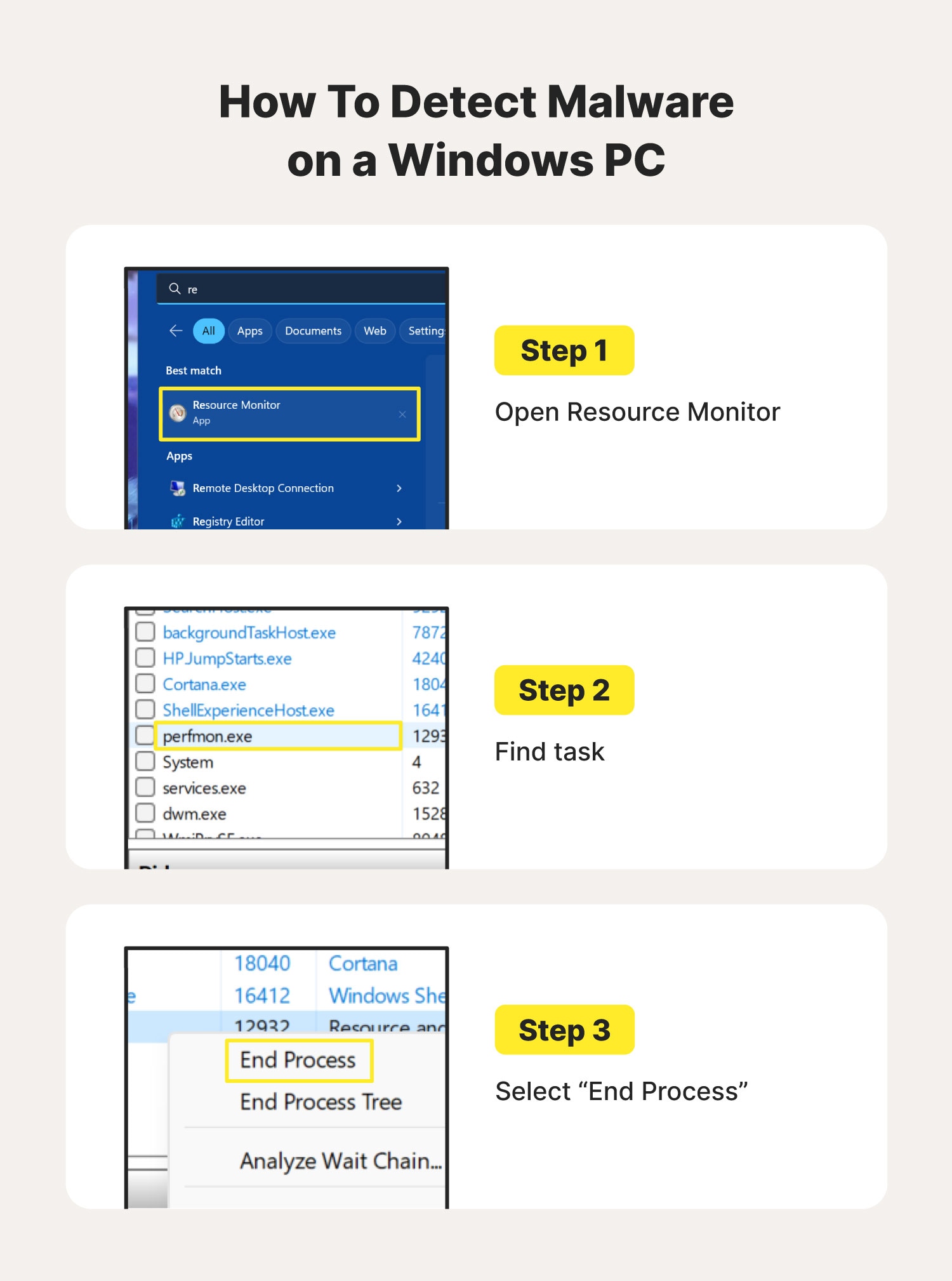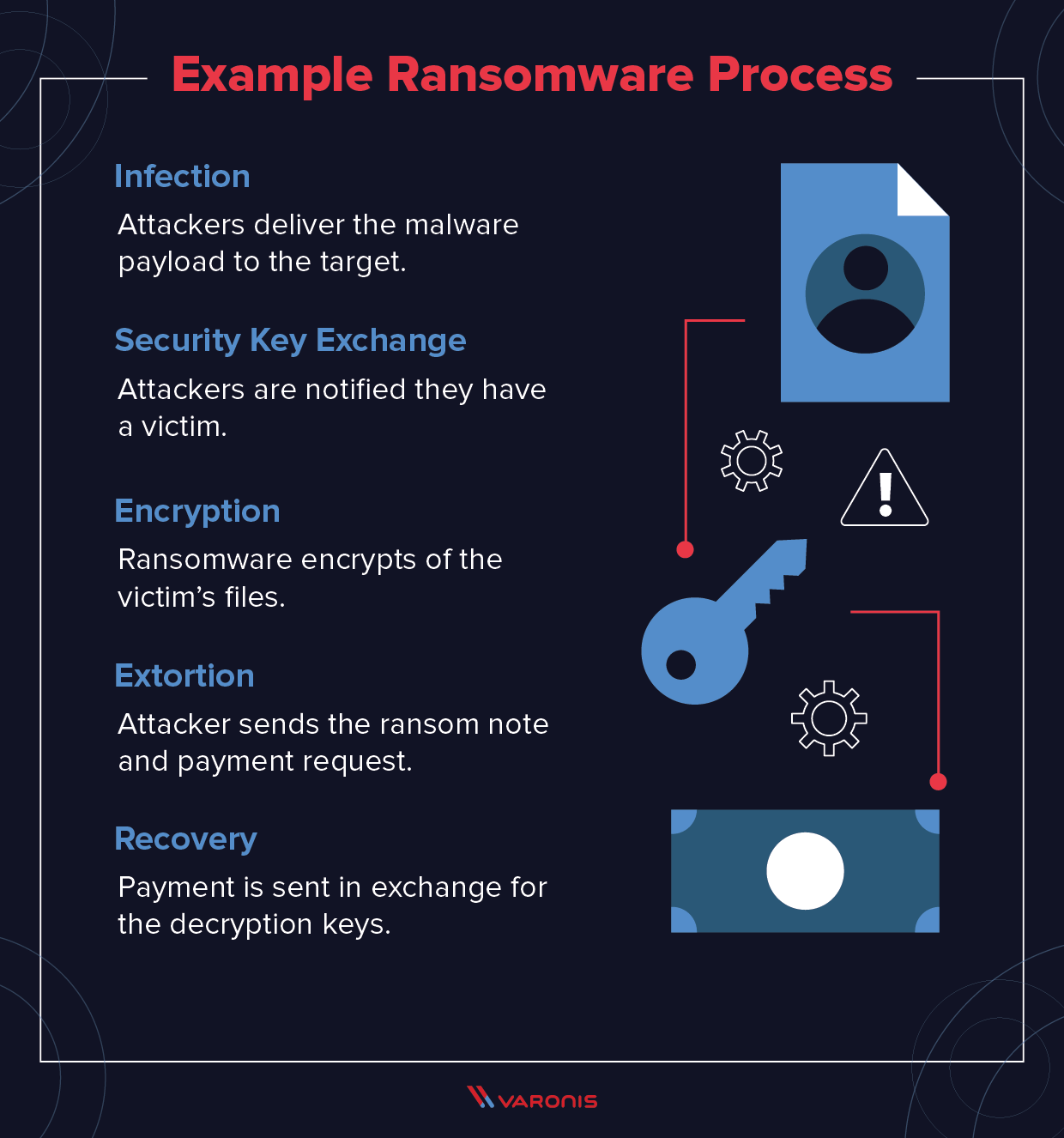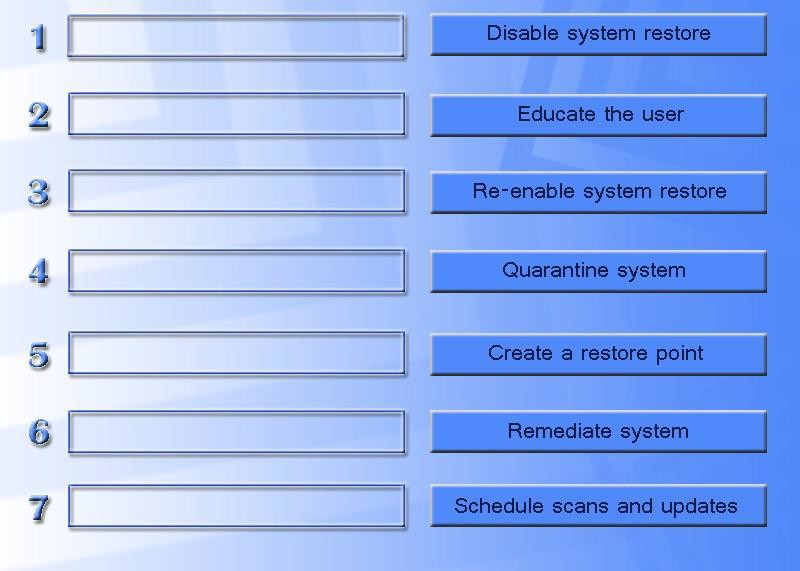
Drag and drop the following malware remediation techniques in the correct order Joe should follow to alleviate this issue.
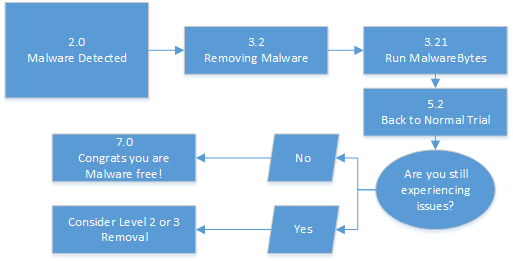
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology

Best Practices for Malware Removal - CompTIA A+ 220-902 - 4.2 - Professor Messer IT Certification Training Courses
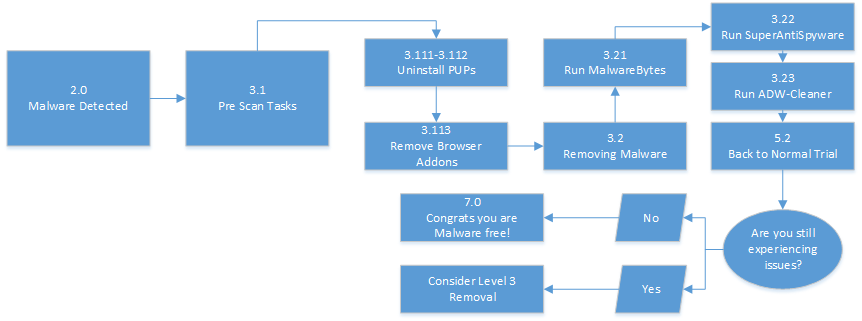
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology